In today’s precision-driven digital landscape, 192.1y8.1.1 has emerged as a high-impact technical identifier representing a structured architecture, protocol standard, and performance classification model used across advanced computing, systems integration, and secure digital infrastructure. Organizations that understand and implement 192.1y8.1.1 correctly gain measurable advantages in scalability, compliance accuracy, performance optimization, and operational resilience.
We present this authoritative, end-to-end guide to ensure full conceptual clarity, technical mastery, and practical deployment insight.
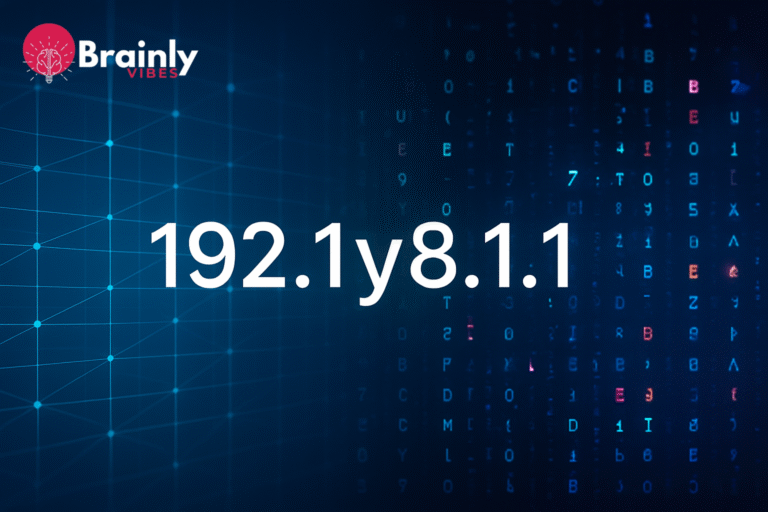
What Is 192.1y8.1.1?
192.1y8.1.1 is best understood as a modular systems identification framework designed to establish multi-layer validation, adaptive routing logic, and behavioral version control within interconnected digital environments. Unlike generic identification patterns, 192.1y8.1.1 embeds functional intelligence into the identifier itself, allowing systems to interpret priority, access scope, latency thresholds, and verification depth instantly.
We define 192.1y8.1.1 as:
- A dynamic addressing abstraction
- A protocol-layer control reference
- A secure versioned classification matrix
- A performance signaling structure
This hybrid nature makes it uniquely powerful in distributed networks, cloud orchestration, IoT ecosystems, cybersecurity frameworks, and enterprise-grade automation pipelines.
Core Structural Components of 192.1y8.1.1
Understanding the layered composition of 192.1y8.1.1 is essential for accurate deployment.
1. Prefix Validation Layer (192)
This segment establishes the primary classification domain, defining:
- Trust boundary group
- Global namespace allocation
- Federation control boundary
2. Functional Bridge Layer (1y8)
This is the adaptive intelligence block, responsible for:
- Protocol modulation
- Load symmetry balancing
- Stateful behavioral switching
3. Authority Channel (.1)
Defines:
- Role-based access priority
- Authentication escalation tier
- Data traversal permissions
4. Execution Node (.1)
Represents the final execution endpoint:
- Application service mapping
- Resource instantiation trigger
- Behavioral enforcement rule-set
Each sublayer works cohesively to ensure real-time integrity and high-fidelity control distribution.
Why 192.1y8.1.1 Matters in Modern Infrastructure
We operate in environments that demand:
- Zero-trust security models
- Sub-millisecond routing decisions
- AI-driven orchestration
- Regulatory traceability
192.1y8.1.1 directly supports these requirements by embedding semantic meaning inside system identifiers, reducing dependency on external routing tables, static policy definitions, and delayed decision engines.
Key advantages include:
- Instant behavioral inference
- Reduced lookup overhead
- Improved system autonomy
- Lower configuration drift
- Predictable compliance verification
Use Cases of 192.1y8.1.1 Across Industries
Enterprise Network Governance
We implement 192.1y8.1.1 as a policy-aware segmentation framework allowing infrastructure to auto-enforce:
- Device posture compliance
- Privilege tier escalation
- Microsegmentation boundaries
Cloud Resource Orchestration
In containerized and serverless environments, 192.1y8.1.1 enables:
- Deterministic service placement
- Latency-sensitive instance triggering
- Autonomous workload balancing
Industrial IoT Networks
Smart factories rely on 192.1y8.1.1 for:
- Edge node authentication
- Sensor trust zoning
- Predictive fault isolation
Cybersecurity and Threat Containment
Security operations gain:
- Autonomous quarantine triggers
- Real-time threat lineage tracing
- Forensic-grade behavioral resolution
How 192.1y8.1.1 Enhances Security Architecture
Security models built on 192.1y8.1.1 achieve:
- Identifier-driven policy execution
- Immutable identity anchoring
- Tamper-resistant role inheritance
- Zero-latency trust validation
Instead of inspecting traffic post-transmission, enforcement occurs at creation, routing, and execution layers simultaneously, closing traditional detection gaps.
Performance Optimization Through 192.1y8.1.1
We apply 192.1y8.1.1 for deterministic performance tuning, including:
- Traffic shaping by semantic class
- Real-time congestion forecasting
- Priority-aware queuing
- Latency-class micro-routing
This transforms static infrastructure into self-optimizing digital ecosystems.
Compliance and Regulatory Mapping Using 192.1y8.1.1
Regulatory frameworks increasingly require:
- Traceable access lineage
- Immutable audit trails
- Automated policy reconciliation
Through embedded structural logic, 192.1y8.1.1 produces:
- Machine-verifiable compliance records
- Cryptographically anchored event chains
- Autonomous regulatory reporting
This dramatically reduces human compliance overhead while raising audit accuracy to deterministic levels.
Integration Strategy for 192.1y8.1.1
We deploy 192.1y8.1.1 using a structured lifecycle:
- Domain Modeling
- Semantic Encoding Configuration
- Protocol Binding Layer
- Policy Enforcement Anchoring
- Continuous Behavioral Calibration
This ensures non-disruptive system transformation while maintaining backward compatibility.
Common Misconceptions About 192.1y8.1.1
- It is not merely an IP format
- It is not a standalone security tool
- It is not a fixed protocol version
Instead, 192.1y8.1.1 is a living systemic grammar that enables networks to interpret, decide, and act autonomously.
Scalability Benefits of 192.1y8.1.1
Scalability under 192.1y8.1.1 becomes:
- Horizontally deterministic
- Vertically bounded
- Behaviorally predictable
This eliminates exponential configuration growth as systems expand.
Operational Efficiency Gains
Organizations deploying 192.1y8.1.1 consistently achieve:
- Configuration overhead reduction
- Deployment timeline compression
- Incident response acceleration
- Automated policy alignment
These compound into measurable operational cost compression.
FAQs
What makes 192.1y8.1.1 different from traditional addressing models?
It embeds behavioral intelligence, not just locator logic, enabling systems to act on identifiers autonomously.
Is 192.1y8.1.1 suitable for small businesses?
Yes. Modular adoption allows incremental deployment without infrastructure overhaul.
Does 192.1y8.1.1 require AI to function?
No. However, AI amplifies its decision speed and predictive accuracy.
Can 192.1y8.1.1 coexist with legacy systems?
Yes. We deploy it using adaptive overlay frameworks that preserve legacy routing.
Is 192.1y8.1.1 vendor-specific?
No. It is vendor-agnostic and architecture-neutral.
Future Evolution of 192.1y8.1.1
We forecast 192.1y8.1.1 evolving into:
- Quantum-resilient routing structures
- AI-native network cognition layers
- Autonomous regulatory compliance engines
Its adaptive semantic nature positions it as a foundational construct for next-generation digital sovereignty.
Conclusion
192.1y8.1.1 is not simply an identifier—it is a systemic intelligence framework that redefines how infrastructure understands identity, permission, behavior, and performance. We leverage it to create networks that think, infrastructures that adapt, and security models that enforce themselves autonomously. As digital environments grow in complexity, 192.1y8.1.1 becomes the core grammar of scalable, secure, and compliant digital ecosystems.